Introduction
Has your code ever been plagued by a mysterious crash or unexpected behavior that’s hard to track down? If so, you may have encountered an address sanitizer issue. Address sanitizers are a powerful tool for detecting memory errors in C and C++ code, but they can be tricky to interpret and fix. In this article, we’ll provide a comprehensive guide to understanding and resolving address sanitizer errors.
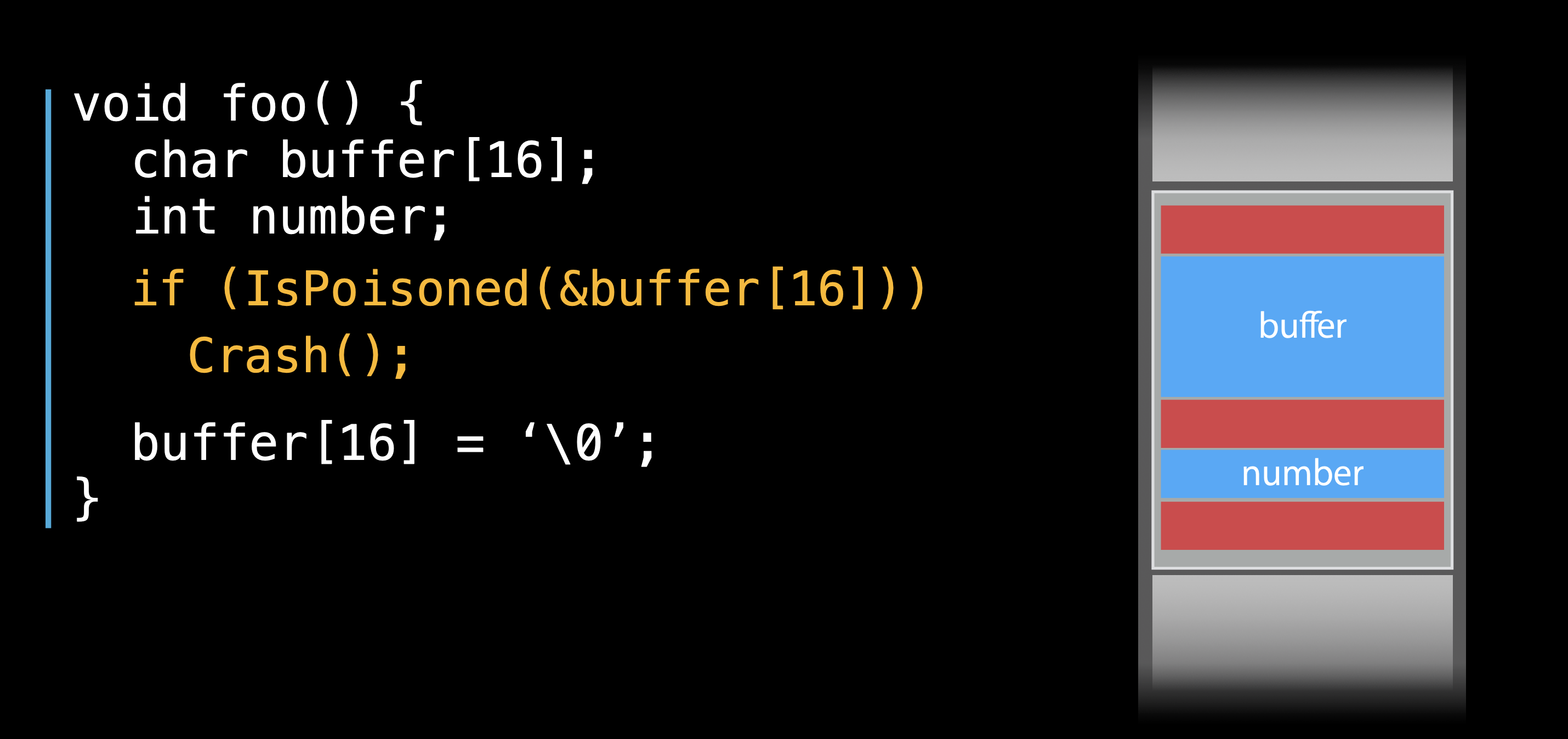
Image: suelan.github.io
Address sanitizers, such as AddressSanitizer (ASan) and MemorySanitizer (MSan), are designed to catch a wide range of memory errors, including:
- Out-of-bounds accesses
- Use-after-free
- Double-free
- Uninitialized memory
- Buffer overflows
Understanding Address Sanitizer Errors
When an address sanitizer detects an error, it generates a report that includes information about the type of error, the memory location where it occurred, and the code responsible for the error.
Here’s an example of an address sanitizer report:
AddressSanitizer: heap-buffer-overflow on address 0x66380000000f at pc 0x7f7ca1429a85 bp 0x7f7ca1429d20 sp 0x7f7ca1429a40
READ of size 1 at 0x66380000000f thread T0
#0 0x7f7ca1429a21 in malloc (/builds/slave/host-x64-shared/zlib-1.2.11/package/bin/..//lib/x86_64-linux-gnu/libz.a)
#1 0x7f7ca1a3588b in ?? () from /usr/local/lib/libdes.so.2.1.0
#2 0x7f7ca1a38205 in ?? () from /usr/local/lib/libdes.so.2.1.0
#3 0x7f7ca1a38a7d in ?? () from /usr/local/lib/libdes.so.2.1.0
[…]
This report indicates that a heap buffer overflow occurred at memory location 0x66380000000f, and it provides a stack trace that shows the source code responsible for the error.
How to Fix Address Sanitizer Errors
Fixing address sanitizer errors can be challenging, but it’s essential for writing robust and reliable code. Here are a few tips to help you get started:
- Understand the error message. The first step is to understand the type of error that occurred and the memory location where it occurred.
- Debug the code. Use a debugger to step through the code and identify the source of the error.
- Fix the code. Once you have identified the source of the error, fix the code by modifying the allocation, deallocation, or access of memory.
- Test the fix. Re-run the code with the address sanitizer enabled to ensure that the error has been fixed.
Expert Advice
In addition to the tips above, here are some additional expert advice for fixing address sanitizer errors:
- Use a memory profiler. A memory profiler can help you identify memory leaks and other memory-related issues that can lead to address sanitizer errors.
- Use static analysis tools. Static analysis tools can help you identify potential memory errors before they cause crashes.
- Attend training or workshops. There are many training courses and workshops available that can teach you how to use address sanitizers effectively.
Image: juejin.cn
FAQ
Q: What is the difference between ASan and MSan?
A: ASan detects a wide range of memory errors, including out-of-bounds accesses, use-after-free, and double-free. MSan detects memory errors that are more specific to multi-threaded code, such as data races and atomicity violations.
Q: How do I enable ASan or MSan?
A: To enable ASan, you can use the -fsanitize=address flag during compilation. To enable MSan, you can use the -fsanitize=memory flag during compilation.
Q: What are the limitations of address sanitizers?
A: Address sanitizers can have a performance overhead, especially for large codebases. They may also not detect all memory errors, especially those that occur in complex code.
How To Fix An Address Sanitizer
Conclusion
Address sanitizers are a powerful tool for finding memory errors in C and C++ code. By understanding how to interpret and fix address sanitizer errors, you can write more robust and reliable code. We encourage you to explore this topic further and share your knowledge with others.
Do you have any questions or comments about address sanitizers? Let us know in the comments section below.